Akamai Guardicore Segmentation
Fast, intuitive microsegmentation for all environments.
Stop lateral movement with granular controls
Akamai Guardicore Segmentation is a software-based microsegmentation solution that provides the simplest, fastest, and most intuitive way to enforce Zero Trust principles. It enables you to prevent malicious lateral movement in your network through precise segmentation policies, visuals of activity within your IT environment, and network security alerts. Akamai Guardicore Segmentation works across your data centers, multicloud environments, and endpoints. It is faster to deploy than infrastructure segmentation approaches and provides you with unparalleled visibility and control of your network.
How does it work?
Using a mix of agent-based sensors, network-based data collectors, and virtual private cloud flow logs to map your network, Akamai Guardicore Segmentation is designed to deliver a single visual of all of your assets and infrastructure — including legacy and modern operating systems, operational technology, and IoT devices. From there, you can easily create and enforce policies that will reduce your attack surface and meet your business needs.
A better way to achieve Zero Trust segmentation
Reduce your attack surface
Reduce risk without the need for costly security hardware with a software-based microsegmentation approach.
Prevent lateral movement
Detect lateral movement and real-time threats across the entire cyberattack kill chain with a single platform.
Secure critical IT assets
Protect critical assets from ransomware by easily enforcing Zero Trust principles across hybrid cloud ecosystems.
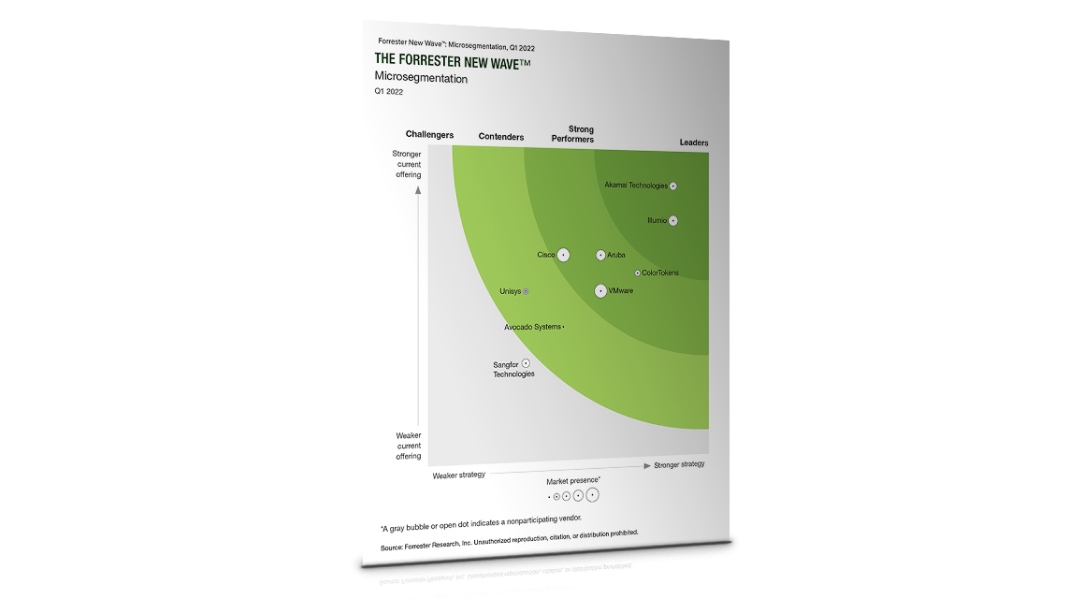
Learn why Forrester named Akamai Guardicore Segmentation a Leader
Features
- Granular segmentation capabilities down to individual processes and services
- Near-real-time and historical visibility makes forensic analysis easier
- Broadest platform coverage for both legacy tech and the latest systems
- Custom threat hunting services provided by Akamai Security Research
- Flexible asset labeling that integrates with orchestration systems and CMDB
- Fast and intuitive policy creation with templates for the most common use cases
- Threat intelligence and breach detection to reduce incident response time
- Osquery-powered insights to detect high-risk platforms and devices in your environment
Malware protection module now available with App & API Protector
Malware protection scans files at the edge to prevent attackers from uploading malware to your systems.

4 Reasons Your Business Needs Zero Trust Architecture
Frequently Asked Questions (FAQ)
It is available either in the cloud or on-prem, enabling you to easily implement your network segmentation strategy into your current architecture.
Yes, you can run your firewalls in parallel with Akamai’s microsegmentation solution. However, Akamai Guardicore Segmentation is a more granular and flexible network segmentation solution that should enable you to remove most of your firewalls, especially your internal ones. Many clients run them in parallel for a short period of time until they are comfortable with the new policy enforcement.
Our microsegmentation solution is agent based. We also have an agentless version for devices where it can’t be installed, such as IoT devices, giving you the flexibility to protect all of your servers, Linux, Windows, and Mac assets. It supports most legacy systems to modern OSs and everything in between, including Windows 7, 2000, and 8, and Kubernetes (K8s).
Policy creation is fast and easy. Using AI, our microsegmentation solution suggests policies through intuitive templates and workflows and allows you to customize them based on your own business needs.
It is a standalone microsegmentation product that protects east-west traffic and enforces one of the core principles of Zero Trust , as defined by both Forrester® and Gartner®. Forrester states that “Microsegmentation Is Essential For Zero Trust Private Networks” in its 2022 Forrester New Wave™.
Akamai provides managed threat hunting services through Akamai Hunt, which finds and remediates the most evasive security risks in your environment. It is led by security experts from Akamai’s threat intelligence and analytics teams — and utilizes the data gathered from the Akamai Guardicore Segmentation solution — to search for threats in your network, find and virtually patch vulnerabilities, and harden your infrastructure.

“Akamai Guardicore Segmentation blew away all the other solutions we looked at because it’s easy to implement at scale and gives us deep visibility into what’s happening inside our network. The ability to search for any user to see where they’ve been and what they’re doing now is extremely valuable for ransomware defense.”
Shane Barnard, Senior Network Engineer, Summit Hosting
Microsegmentation Use Cases
Learn how microsegmentation provides critical application ringfencing, control over third-party access, AWS cloud compatibility, Docker and Kubernetes container security, threat detection and response, and Zero Trust segmentation policy management.
Critical Application Ringfencing
Focused protection of the applications you rely on most
Most organizations have a select set of applications that are the lifeblood of their business, from customer-facing web applications to databases containing valuable or sensitive information. Security incidents affecting these types of critical assets can have a significant impact on a company’s business and reputation. Akamai helps security teams give critical applications the security focus they require by providing a visual map of how they work, making it easy to ringfence them with precise segmentation policies, and protectively detecting targeted attacks.
Benefits:
- Visualize critical applications in detail — Understand how critical applications work and communicate, so you can protect them effectively.
- Create granular ringfencing policies — Tightly control how applications function and isolate them to the greatest extent possible.
- Detect and respond to attacks quickly — Employ multiple complementary techniques to detect and mitigate attacks against critical assets.
Third-Party Access Control
Tightly manage IT resource access based on business need
Akamai Guardicore Segmentation gives you precise visibility and control over third-party access to your IT environments. Akamai’s rich application visualization capabilities, which incorporate contextual labels from orchestration tools and other data sources, make it easy to understand the function of specific applications. Armed with these insights, security teams can implement granular policies that limit application access to specific Active Directory users and groups. This allows organizations to support third-party access needs while limiting security exposure.
Benefits:
- View applications by function — See applications and their communication in context on a customizable visual map.
- Control third-party user access — Narrowly limit users’ access to only those applications that they have a clear business need to use.
- Detect possible user account abuse — Receive timely alerts and supporting information when unsanctioned account usage attempts occur.
AWS Microsegmentation Solution
Simplify the shared responsibility model with AWS cloud security
Akamai is an Advanced Technology Partner for AWS microsegmentation, with security competency. As a powerful third-party tool, Akamai Guardicore Segmentation uses deep visibility to map your entire IT infrastructure and its communication and dependencies in an intuitive way. This map supports a multicloud and hybrid cloud infrastructure, helps teams to ensure that their security posture is maintained, and confirms that they understand how their applications and environments interact and depend on each other. It also provides the basis for building a smart, flexible, and tight microsegmentation security policy. Altogether, Akamai makes the shared responsibility model of the AWS cloud simple to manage and maintain.
Benefits:
- Fully integrated microsegmentation solution for AWS allows users to see native-cloud information and AWS-specific data on the dashboard.
- Granular visibility at process level adds visibility to your instances down to the process level.
- Take your microsegmentation beyond AWS with simple microsegmentation policies that span regions and VPCs, containers, VMs, and on-premises.
Container Security
Seamless, comprehensive security solution for containerized applications
Akamai Guardicore Segmentation provides comprehensive container security for teams using any blend of Docker and Kubernetes. Akamai protects containerized applications, empowering DevSecOps teams with various critical capabilities without sacrificing the organization’s security posture. Akamai secures the production and operational elements of containers by enabling visibility into every container, visualization of communication flows, and security with microsegmentation policies.
Benefits:
- Gain visibility and discover every pod and container communication flow.
- Apply segmentation policies based on native pod labels that ensure security controls scale and migrate with containers.
- Protect containerized applications in PCI-sensitive workloads and demonstrate compliance.
Threat Detection and Response
Detect more threats faster and respond with greater intelligence
Today’s rapidly expanding clouds and data centers have become prime targets for infiltration and attacks with alarming frequency. Security teams are hard-pressed to keep pace with the staggering rate of breaches. Akamai Guardicore Segmentation is the only microsegmentation solution that provides a single, scalable platform with real-time threat detection and response capabilities, featuring the following key attributes:
- Multiple detection methods
- Made for the cloud
- Integrated response
- Detailed forensics
Benefits:
- Multiple threat detection methods address all types of threats.
- Investigate threats with automatic analysis and high-fidelity incident data.
- Respond to attacks with mitigation recommendations, while platform integrations accelerate incident response.
Zero Trust Segmentation
Discover application dependencies to reduce attack surface, secure critical applications and ensure compliance
A solid foundation for workload protection and compliance is the granular isolation and segmentation of your network applications and their components. Akamai Guardicore Segmentation enables deep application dependencies mapping and policy enforcement, ensuring an ongoing management process of your microsegmentation policy. It delivers one of the industry’s most complete and flexible solutions for microsegmentation, featuring the following key attributes:
- Wide coverage
- Deep visibility
- Intuitive workflow
- Granular policies
Benefits:
- Visibility of your environment through application discovery and dependency mapping to understand the distinction between what should and should not be trusted.
- Enforce Zero Trust principles with quick-to-design, -test, and -deploy policies.
- Track and monitor your network with threat intelligence, alerting, and more.
Zero Trust for Connected Devices
Secure your IoT/OT devices at scale
Securing IoT and OT devices has traditionally been a challenge for most organizations. With Akamai Guardicore Segmentation, organizations are now able to reduce their attack surface and enforce Zero Trust policies on devices that can’t run host-based security software. Major features include:
- Continuous device discovery
- Integrated device fingerprinting
- Deep visibility
- Agentless Zero Trust segmentation
- Roaming device awareness
Benefits:
- Discover, visualize, and map all IoT and OT systems alongside your IT infrastructure in a single view.
- Identify and segment high-value systems to protect them from the spread of breaches. No third-party security tool is needed.
- Assign every device its own fingerprint to ensure that appropriate security policies are applied.
- Prevent and contain ransomware and other malware attacks by applying least-privilege segmentation policies to the network before an attack occurs.



